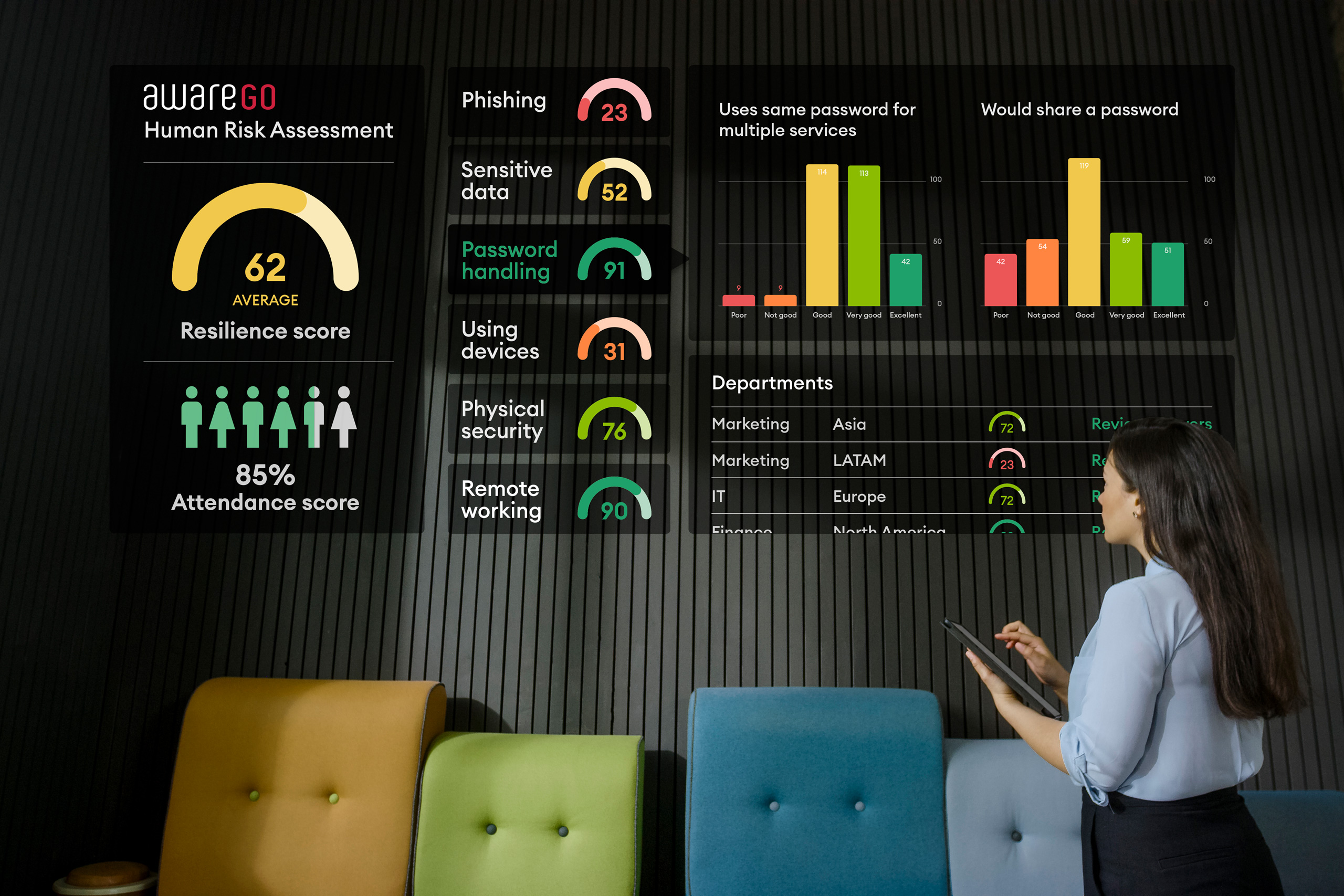
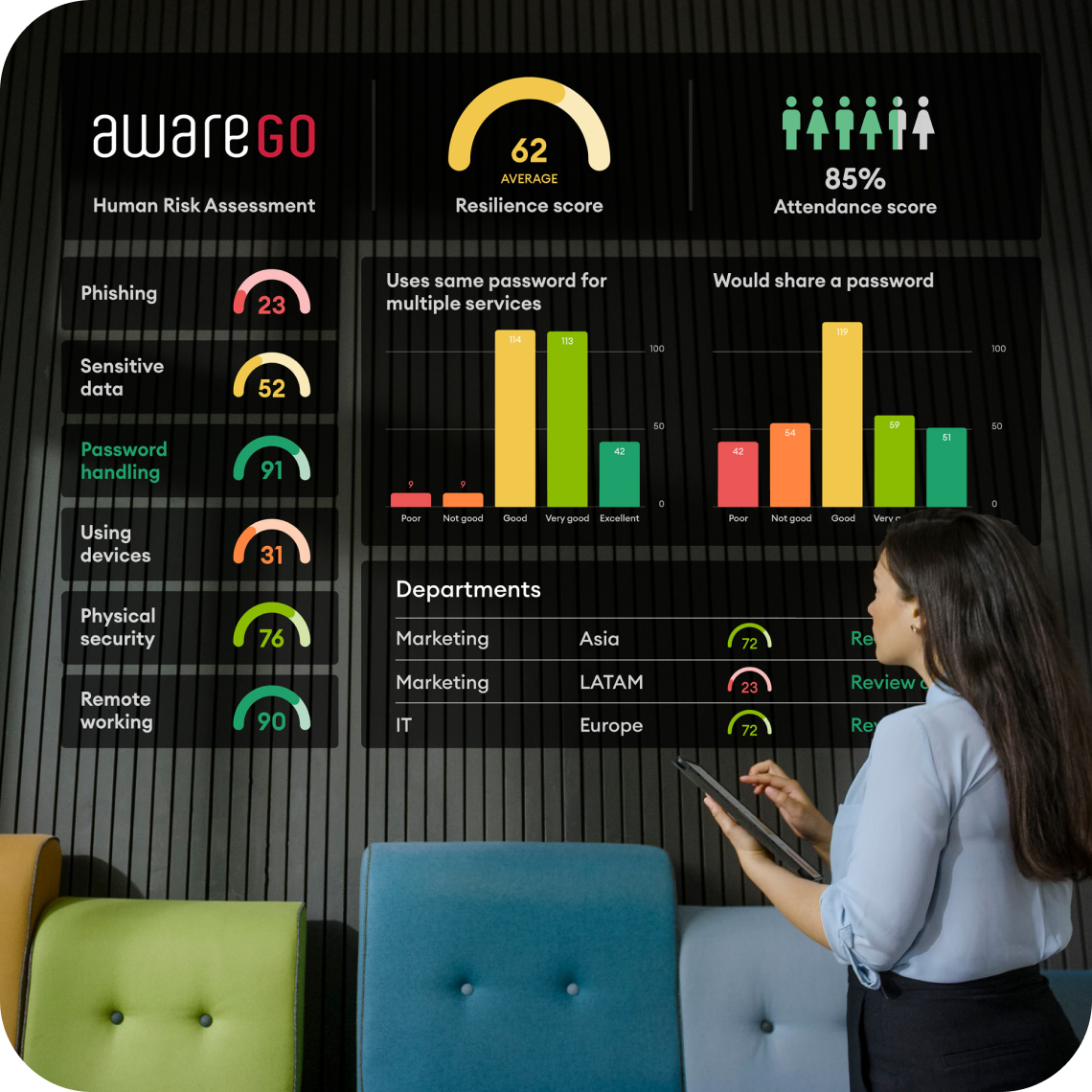
Cyber Security Awareness training is essential for companies and their employees but can be a daunting task. The right training introduces the needed security awareness topics to people without lecturing, scaring or shaming them. Cyber security awareness training, when correctly done, should be empowering and benefit employees both at work and at home.
A few years ago the new General data protection regulation (GDPR) took effect in Europe. Not only is GDPR compliance necessary for all companies, but this new regulation also makes it mandatory for most organizations to assign a dedicated Data Protection Officer (DPO) to handle their data security affairs.

There are a lot of things to consider with regards to GDPR, cyber security awareness training program for your employees being one of the most crucial things. That’s where we can help.
What You Need to Know
It is crucial that all your employees are aware of the cyber security threats out there. Therefore, to give you an idea of what kinds of things your organization is dealing with, we’ve compiled this Top 10 List of Cyber Security Awareness Topics – the kinds of things everyone in your organization needs to be aware of today!
1. DATALEAKS
![]() We are human, and the fact is that behind all data leaks there is a human error.
We are human, and the fact is that behind all data leaks there is a human error.
Everyone makes mistakes but training on the right cyber security awareness topics guides employees on how to react to and report a leak. It can also be hard and embarrassing to admit mistakes. That’s why creating an environment that encourages employees to report mistakes and possible leaks is very important (even if it was an accident or not their responsibility).
Duration matters when it comes to data leaks. The longer a bucket of personal or sensitive information stays open the more significant the threat of the leak. Failure to report a leak can have severe consequences for the individual and lead to hefty fines for the company.
2. SOCIAL ENGINEERING

You are at the largest yearly conference in your industry. You are having fun meeting other people in similar positions and discussing how they are doing things, sharing failures and achievements and learning from each other. However, after a few drinks, the sharing can go overboard, and sensitive information may be discussed and shared.
The intention of the sharing was not bad or malicious. You might not realize the serious consequences it can have if the other person is dishonest and shares classified information with someone else.

To practice good cyber security awareness, it is essential never to discuss confidential work issues with unauthorized people, even if you trust them.
3. PHISHING
![]() If you open an email that happens to be a fraudulent phishing email you are just one of 8 million people in the same situation this very day.
If you open an email that happens to be a fraudulent phishing email you are just one of 8 million people in the same situation this very day.
Phishing is the attempt to obtain sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity.
The word “Phishing” is a newly coined expression created as a homophone of fishing due to the similarity of using bait in an attempt to catch a victim. Every person that has an email address can get a phishing email. That’s why phishing is a security awareness topic that needs to be well introduces at every organization.
Phishing attacks are typically carried out by email spoofing or instant messaging. They often direct users to enter personal information at a fake website which looks and feels identical to the legitimate one – the only difference may be the URL of the website in concern.
4. TAILGATING
![]() John, a former employee of the company you are working for, comes running just when you were about to close the door. He says he’s on his way to meet his former boss. You chat for a minute or two, and then he heads towards the bosses office.
John, a former employee of the company you are working for, comes running just when you were about to close the door. He says he’s on his way to meet his former boss. You chat for a minute or two, and then he heads towards the bosses office.
If you remember correctly, John was pretty angry when he got laid off two months ago. What you might not realize is that John, who knows his way around the company, is about to steal some sensitive information as an act of revenge. This can also be part of an insider risk.
Tailgating threats used to be related to thieves stealing physical things by following an authorized person into a secure location. However, in today’s digital society tailgating is often combined with stealing sensitive information which can lead to serious financial consequences for companies.
The threat is usually associated with former employees, thieves, vandals or people that have issues with the company or employees.
5. PASSWORDS

Passwords are one of those security awareness topics that everyone needs to know about. We all need to come up with multiple passwords for multiple accounts that we can easily remember, and it is getting harder and harder to come up with something innovative.
But passwords are crucial to protect your workstation. To create strong passwords it is best to use a combination of lowercase and uppercase letters, symbols, and numbers.

It can make your life easier to come up with a sentence and use one letter from every word. If the system allows it you could also string together unrelated words to create a passphrase.
6. CEOSCAM
![]() You are browsing through your emails when you notice an email from your the CEO. He claims to be in a hurry and needs you to transfer money to his account quickly.
You are browsing through your emails when you notice an email from your the CEO. He claims to be in a hurry and needs you to transfer money to his account quickly.
You quickly transfer the money… But then you notice something strange; his email address is not even from your company.
This scam is a type of phishing, where cyber criminals spoof company email accounts and try to fool an employee, especially in accounting or HR.
Always double check unusual requests from your boss, especially regarding a financial transfer. It’s very important to be cautious of this when learning about cyber security awareness.
7. RANSOMWARE

Ransomware is a malware or a virus that encrypts the data on your computer or in some cases your whole network. After that, you cannot access your files or pictures, until you pay the ransom, and in some cases not even then.
The most common delivery mechanism of ransomware is by using a phishing scam, attachments sent via email, masquerading as a file you should trust. After they are downloaded and opened, they can take over your computer.
In some cases, ransomware is delivered to your computer via compromised websites which you think you can trust.
If you get infected, there is a small chance you may be able to recover. Check out No More Ransom for instructions.
Best practices to guard against ransomware:
- Keep a backup of your files and backup regularly.
- Do not install software unless you know exactly what it is and what it does.
- Update your operating system and programs when prompted.
- Never run updates in a browser window.
8. PRINTOUTS

Printing out documents is part of the job. But printers are sometimes located in open spaces where a lot of people can have access to them.
It is important to properly dispose of your unused documents, failed prints and not to leave them in the printer tray unsupervised for an extended period.
Information in these documents can be worth a lot of money to the wrong people.
9. DUMPSTERDIVING
![]() Most companies make special efforts to keep certain types of information secret. This information can include customer lists, financial records, employee and payroll records, product development plans, and many other types of confidential information.
Most companies make special efforts to keep certain types of information secret. This information can include customer lists, financial records, employee and payroll records, product development plans, and many other types of confidential information.
Methods used to protect confidential information can include high-security file cabinets, card reader systems used to control access to sensitive areas, and encrypted fax machines used to send and receive confidential information.
Despite precautions, the employees of many companies continue to throw sensitive information into the trash or recycle bins. If you don’t think this is a problem at your company, make random inspections of your outgoing waste – I guarantee you will be surprised!
It is important to understand that while the information found in your trash bin on any one day may not be significant, the cumulative information gathered over a period of time can be extremely damaging. For example, finding a copy of a few invoices in the trash wouldn’t provide your competitor with a complete list of your customers, but having several months worth of your invoices probably would.
Here are some tips for you to consider:
- Conduct periodic inspections of your outgoing trash and recycle bins.
- Provide cyber security awareness training for all employees concerning the proper handling and disposal of confidential information.
- For best security, consider the use of a “DOD Specification” shredder.
- If you have large volumes of documents that must be shredded, you may wish to consider the use of a “document destruction” service.
- Watch out for information thrown in “recycle bins”.
- Make sure that all shredded material is recycled.
- Keep trash and recycle containers locked.
10. WIFI AT HOME & OPEN WIFI
![]() A home network is often set up in a rush to get connectivity ready as soon as possible. Most people do not take any steps in securing their home network, which often makes them accessible to hackers. This can be both a personal risk and a risk to your organization if people are working from home.
A home network is often set up in a rush to get connectivity ready as soon as possible. Most people do not take any steps in securing their home network, which often makes them accessible to hackers. This can be both a personal risk and a risk to your organization if people are working from home.
A router is usually just a small computer with its own operating systems, software and vulnerabilities. Routers often advertise their type and make directly in the Wireless name (SSID) which makes it easier for hackers to see which type the router is. This may even make it easier for them to get information about how to hack it.

Changing the router SSID and the admin username and password is the first step in cyber security awareness to secure your home WiFi. Updating a router’s firmware is something that should be done on a regular basis. Most routers fail in notifying users that an update is available even though those updates are essential to patch security holes. It can also be necessary to restart the router every once in a while. Securing the home network is a security awareness topic that benefits people both in their private and professional lives.
A stolen mobile device is also a risk to both home and office WiFi as the device has direct access to the networks it is connected to. Remotely wiping a stolen device is something that should be done as soon as possible, according to best cyber security awareness practices.
Open WiFi
Finally, using free public WiFi networks comes with a number of security risks, but an overwhelming majority of people use it without hesitation. The same features that make them desirable for consumers make them desirable for hackers.
The most common threat to public WiFi is the possibility for the hacker to position himself between you and the connection point, making all your traffic go directly through the hacker’s computer. That way it is easy for them to catch passwords or data that is not encrypted.
Hackers can also use public WiFi to distribute malware. If you allow file sharing on your computer, it is quite easy for a hacker to plant infected software on your computer.